Did you know that 56% of SMEs experienced cybersecurity incidents in 2022? Over 185,000 successful attacks targeted the information systems of French organizations in 2022, which is more than 1,000 per day! And among these attacks, more than 90% were carried out via email, with 80% in the form of phishing!
Phishing is an attack technique aimed at stealing sensitive information from users. By impersonating trusted entities, cybercriminals entice their victims to click on malicious links or disclose personal data.
This article aims to shed light on the various most frequent forms of phishing, the potential dangers, and above all, the best practices to protect yourself.
I. What is phishing?
Phishing relies on manipulation and social engineering (persuasion scenario) to deceive users. Hackers imitate the identity of legitimate organizations, such as banks, administrations, social security agencies, or well-known companies, to gain the trust of their victims.
Their modus operandi revolves around various channels:
- Emails: The most common vector (80% of attacks), often in the form of urgent messages or account notifications. For example, you receive an email from the Family Allowance Fund informing you that you are going to receive your benefits and asking you to log in to your account by clicking on a fake link…
- SMS: “Smishing” attempts to phish users via fraudulent SMS messages. A recent example: a fake message from your bank asking you to update your information or a message from a delivery organization (DHL, LaPoste…) with a link to track the progress of the delivery…
- Websites: Counterfeit websites mimicking legitimate platforms to capture sensitive information. These sites use the same design as the sites they imitate and it is often difficult to see the difference.
- Phone calls: “Vishing” consists of deceiving victims by telephone by posing as a customer service or an authority. Elderly people are particularly vulnerable to this type of attack, with criminals posing as bank employees, telephone company employees… but anyone can be a victim of this type of attack.
During a phishing attack, criminals will often ask you for the following types of information:
- Date of birth
- Social Security number
- Phone number
- Postal address
- Credit card details (on a fake bank website, for example)
- Your login details
- Your password…
II. The different forms of phishing
The general term phishing actually includes several variants, each targeting specific objectives:
- Classic phishing attacks: aim to obtain personal information, sensitive information such as your bank details.
- Spear phishing attacks: target specific individuals within an organization. This type of attack often takes place in several stages, the objective being little by little to gain the trust of individuals to obtain sensitive data.
- Whale phishing attacks: target business leaders for significant gains. The term Whale referring to the potential gain that criminals hope to recover.
- Ransomware attacks: combine phishing with malicious software to encrypt data, sometimes block your computer remotely and extort a ransom in exchange for giving you access to your data and/or computer. This type of attack can take place over several months, with criminals collecting information in the process to carry out future attacks.
- Typosquatting attacks: exploit spelling errors in domain names to redirect to fraudulent sites. Example: Peypal instead of Paypal, neteflix.com or netflix.org to counterfeit the site netflix.com
Whatever form the criminals take, it is always a matter of exploiting the credulity of the victims, the habits, the lack of vigilance to achieve their end.
How to spot a fraudulent email or a Phishing site:
- An email from a service or website that you are not a customer of.
- An email from a trusted source but with many spelling mistakes.
- An unusual sender name or address.
- An email with a subject that is too good to be true, an offer that is too good to be true.
- A suspicious appearance.
- An absence of personalization.
- An unusual request.
- A request for confidential information.
- A worrying message.
- An incentive to click on a link.
Example of emails that should alert you:
- Request for update or confirmation of personal data – identifiers, passwords, bank details… – by a supposed public or commercial organization of trust, under penalty of sanction.
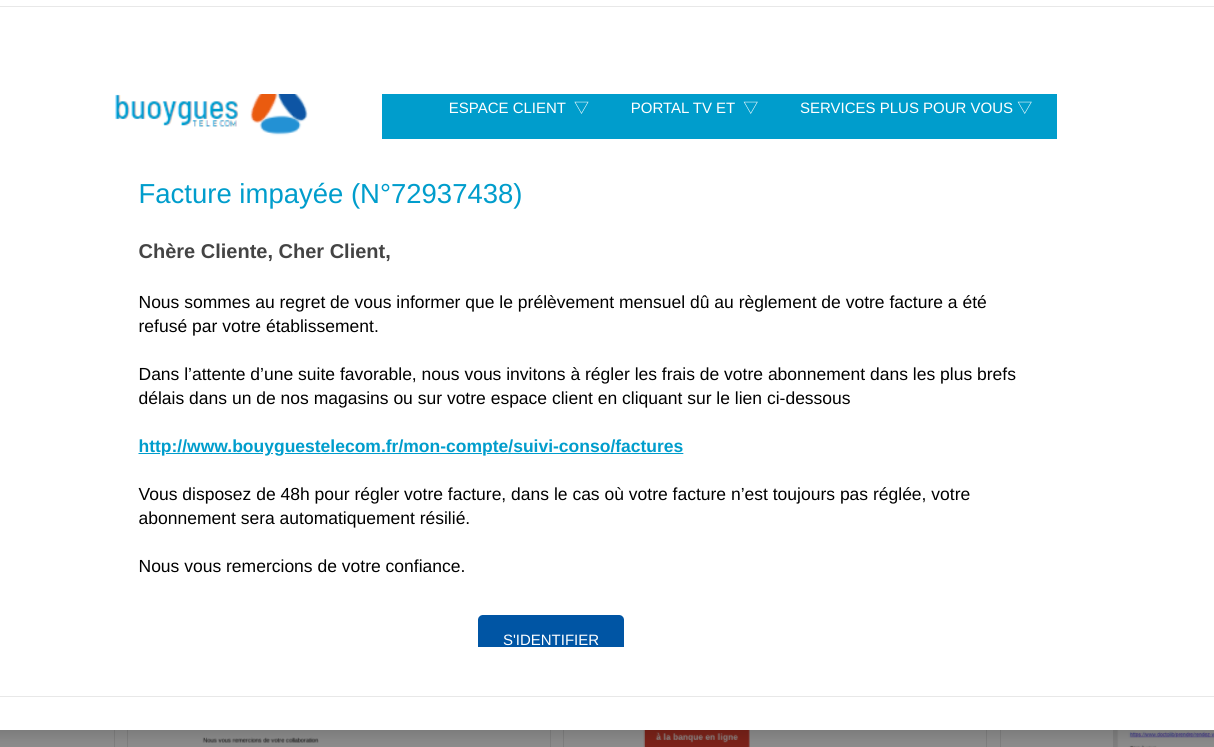
- Payment default or billing problem: a fake email informs you that a good cannot be shipped due to a billing problem or that you must pay unpaid.
- Unexpected request for information for a refund, a cancellation of order, a delivery, etc.
- Request for information in exchange for sending a gift or to participate in a competition with an attractive prize, or to recover the winnings of a lottery.
- Request for payment to avoid the closure of an access, the loss of a domain name or a supposed RGPD compliance.
- Fraudulent calls for donations.
- Call for help: the cybercriminal poses as a loved one, explaining that he is in a disastrous situation that requires your financial assistance.
- Chain emails of the lucky charm type, financial pyramid, call for solidarity or viral alert, can conceal a phishing attempt.
Exemple :
III.The dangers of phishing
The consequences of a phishing attack can be severe and costly:
- Theft of personal data: login credentials, credit card numbers, sensitive information.
- Identity theft: use of stolen information to commit fraud.
- Infiltration of computer systems: installation of malware to infect devices.
- Embezzlement of funds: unauthorized transfers of money from bank accounts.
- Damage to reputation: loss of trust from customers and partners for companies.
French law mentions the following offenses:
In the Penal Code
- Identity theft (Article 226-4-1): the fact of usurping the identity of a third party or making use of one or more data of any kind allowing to identify him with a view to disturbing his tranquility or that of others, or to harm his honor or his consideration, is punishable by a sentence of one year’s imprisonment and a fine of 15,000 euros.
- Collection of personal data by fraudulent, unfair or illegal means (Article 226-18: such collection constitutes an offense punishable by a prison sentence of five years and a fine of 300,000 euros.
- Fraud (Article 313-1): fraud is the fact, either by the use of a false name or a false quality, or by the abuse of a true quality, or by the use of fraudulent maneuvers, to deceive a natural or legal person and thus determine him, to his prejudice or to the prejudice of a third party, to hand over funds, securities or any property whatsoever, to provide a service or to consent to an act operating obligation or discharge. Offense punishable by a prison sentence of five years and a fine of 375,000 euros.
- Fraudulent access to an automated data processing system (Article 323-1): the fact of accessing or remaining, fraudulently, in all or part of an automated data processing system is punishable by two years’ imprisonment and a fine of 60,000 euros. When it resulted either in the deletion or modification of data contained in the system, or in an alteration of the functioning of this system, the penalty is three years’ imprisonment and a fine of 100,000 euros.
In the Monetary and Financial Code
Counterfeiting and fraudulent use of means of payment (Articles L163-3 and L163-4): offense punishable by a prison sentence of seven years and a fine of 750,000 euros.
Finally in the Intellectual Property Code
Counterfeiting of trademarks (logos, signs, emblems…) used during phishing (Articles L.713-2 and L.713-3): Offense punishable by a prison sentence of three years and a fine of 300,000 euros.
United States
Key Laws:
- Computer Fraud and Abuse Act (CFAA): This is the primary federal law addressing computer crimes, including unauthorized access and fraud. Phishing often falls under this act, especially when it involves accessing systems without permission or exceeding authorized access.
- Identity Theft and Assumption Deterrence Act: This law makes it a federal crime to knowingly transfer or use, without lawful authority, a means of identification of another person with the intent to commit, or to aid or abet any unlawful activity that constitutes a violation of Federal law, or a felony under State or local law. Phishing often aims to steal such information.
- CAN-SPAM Act: While primarily focused on commercial email, it also covers some aspects of deceptive or misleading email practices which can be relevant to phishing.
- FTC Act (Section 5): The Federal Trade Commission (FTC) has broad authority to regulate unfair or deceptive acts or practices in commerce. Phishing schemes, due to their deceptive nature, often violate this act.
Consequences: Penalties can include fines, imprisonment, and civil lawsuits. The severity depends on the scale and impact of the phishing attack. For instance, CFAA violations can carry substantial fines and prison terms, especially if the offense involves damage to computer systems or the theft of valuable data.
United Kingdom
Key Laws:
- Computer Misuse Act 1990: This is the UK’s main legislation against computer misuse, covering unauthorized access, modification of data, and other cybercrimes. Phishing activities, particularly those involving unauthorized access to systems or data, are covered by this act.
- Fraud Act 2006: This act deals with various forms of fraud, including obtaining information dishonestly. Phishing schemes that aim to deceive individuals into revealing personal or financial information would likely fall under this act.
- Data Protection Act 2018 (and GDPR): While not specifically about phishing, these laws govern the processing of personal data. If a phishing attack leads to the theft of personal data, the organization that lost the data could face penalties for breaches of data protection laws.
Consequences: Penalties can include fines, imprisonment, and civil lawsuits. The severity depends on the nature of the offense and the extent of the damage caused.
International Law and Cooperation
Budapest Convention on Cybercrime: This treaty provides a framework for international cooperation against cybercrime, including phishing. It aims to harmonize national laws and facilitate cross-border investigations. Many countries have ratified this convention.
Europol and INTERPOL: These organizations play a crucial role in international law enforcement cooperation against cybercrime, including phishing. They facilitate the sharing of information and coordinate investigations across borders.
IV. How to protect yourself from phishing?
A. Awareness and vigilance
The first line of defense lies in raising awareness of phishing techniques.
Remain vigilant against any suspicious message, even if it comes from a seemingly reliable source.
B.Check the sender and the URL
Carefully examine the email address and the URL of the website before clicking.
Beware of suspicious addresses or those with spelling errors.
C. Never disclose sensitive information
No legitimate entity will ever ask you for your login credentials or bank details by email, SMS or phone.
D. Hover over links before clicking
Never click directly on a suspicious link. Hover your mouse over the link to display the destination URL and verify its legitimacy.
E. Install an antivirus and anti-phishing software
Use effective antivirus and anti-phishing software to detect and block online threats.
F. Stay informed of the latest threats
Stay informed of new phishing techniques by consulting reliable sources and following the recommendations of cybersecurity authorities.
G. Enter false data on important sites
A trick when you have a doubt about the identity of the site you are on, in the login area, enter a fake username, a fake email address or a fake password. If you manage to enter the site despite this, the site is not an official site: indeed, if Phishing sites perfectly reproduce the design of the sites they imitate, they do not have access to the databases (data recovery being the objective of the attacks), and therefore they cannot have your usernames and passwords.
V. What to do in case of a phishing attack?
- Do not reply to suspicious emails or SMS messages.
- Do not click on any links or attachments.
- Change your passwords immediately if you think they have been compromised.
- Report the attack to the cybersecurity authorities.
- Contact your bank or payment service if you suspect fraud.
Some useful links:
- Le guide de prévention contre les arnaques
- Site www.cybermalveillance.fr
- Phishing-initiative.fr
- Signal-spam.fr
- Info escroqueries au 0 805 805 817 (Free of charge number)
- signal.conso.gouv.fr
Phishing is a constant threat, but by adopting increased vigilance and following best practices, you can minimize the risk of being a cyberattack victim. Do not hesitate to contact us if you plan to implement training or if you need advice on that matter.
Sources : Mailinblack.com. Rapport du Sénat sur la Cybersécurité dans les entreprises françaises, Rapport Global Security Outlook 2022 du World Economic Forum, Panorama de la Cybermenace de ANSSI, Étude Ipsos et Terranova Security., cybermalveillance.gouv.fr

